Security guaranteed?
“Despite being subject to a legal obligation to ensure that suppliers who process personal data have in place appropriate arrangements to protect that data, a majority of organisations admit to failing to take any steps to assess this. Supply chain breaches present a significant risk to organisations and data controllers should be in a position to demonstrate that they have carried out their due diligence. ”
In recent weeks we have seen a slew of cyber attacks and consequent personal data breaches targeting supply chains, from the Ministry of Defence to Live Nation subsidiary Ticketmaster and Santander. We have published our incident response Helping Hand Checklist, but what measures can be taken to avoid a data breach or at least to insulate yourself against the legal and regulatory risk of an incident?
While the risks aren’t limited to personal data, but also apply to trade secrets and other confidential information or commercially sensitive data, in relation to personal data third party suppliers are likely to be data processors for the purposes of the UK GDPR and Data Protection Act 2018. Article 28(1) UK GDPR obliges data controllers to only use processors “providing sufficient guarantees to implement appropriate technical and organisational measures” to comply with the UK GDPR and ensure that data subjects’ rights are protected.
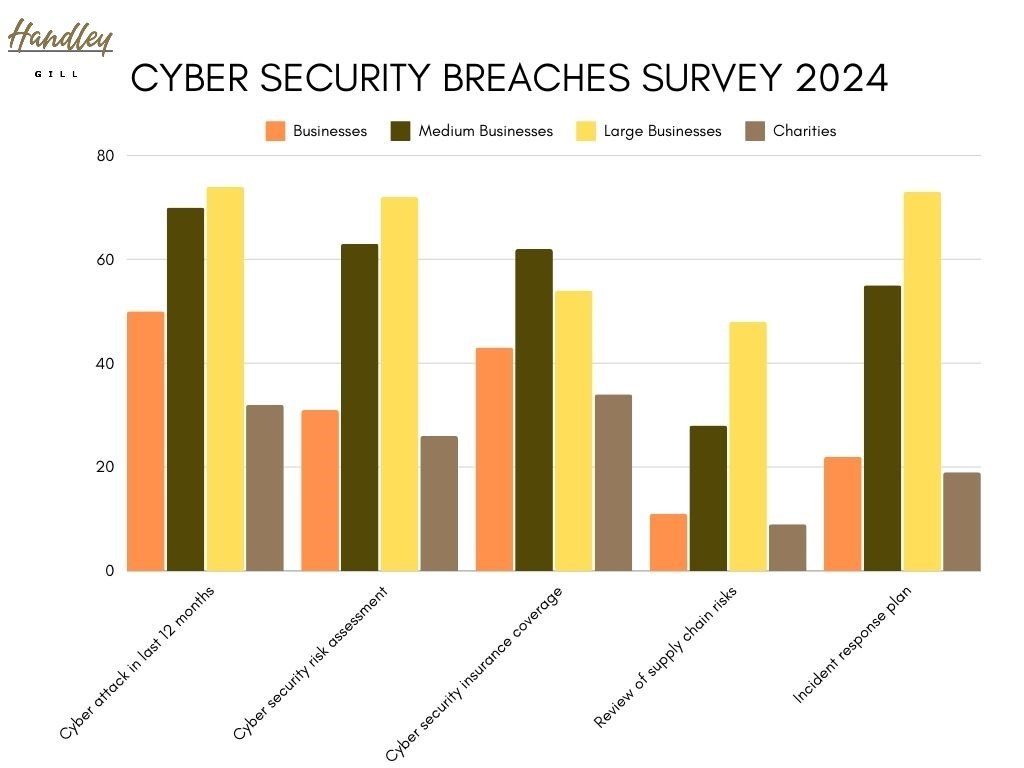
Despite this legal obligation, and the evident threat, the Department for Science, Innovation & Technology’s Cyber Security Breaches Survey 2024 revealed that just 11% of businesses and 9% of charities reviewed the risks posed by their immediate suppliers. Even in relation to large businesses, which are likely to be responsible for larger volumes of personal data, less than half reported conducting supply chain risk assessments.
Department for Science, Innovation & Technology (DSIT) Cyber Security Breaches Survey 2024
Many of the principles of conducting a supply chain risk assessment will also be relevant to an organisation’s own data security practices, but given that the survey also revealed that only 31% of businesses and 26% of charities had conducted their own cyber security risk assessment in the previous year, it is not surprising that even fewer organisations had looked to their suppliers.
Data security is not limited to cyber security, however, and physical security is also important; the ICO’s data security incident trends data reveals that the majority of reported data breaches were non-cyber, although cyber incidents rose by 33% year on year.
We have previously highlighted a range of measures that data controllers can take to improve their supply chain security, the first of which was to “Conduct due diligence in relation to vendors prior to engaging them”. But what does that look like?
Assessments will have both binary and qualitative elements, and while the nature and extent of due diligence that is necessary and appropriate will vary having regard to the nature and sensitivity of the data being processed and the level of access granted to suppliers, and we would advocate a risk-based approach. To coincide with London Tech Week 2024, one of the key themes of which is ‘The Future of Security and Data’, we are publishing our Helping Hand Checklist to conducting a cyber security risk assessment on data processors/supply chain, which has been developed having regard to the National Cyber Security Centre’s (NCSC’s) guidance.
Find out more about our data protection and data privacy services.